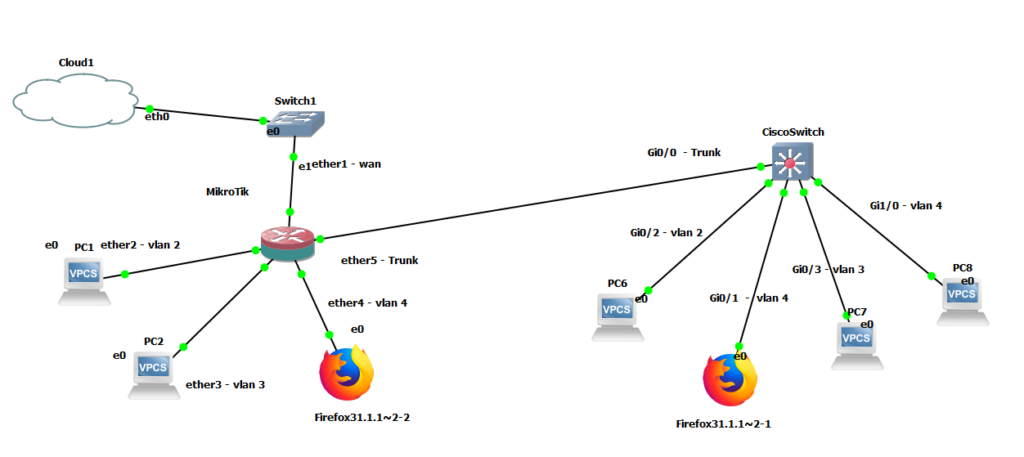
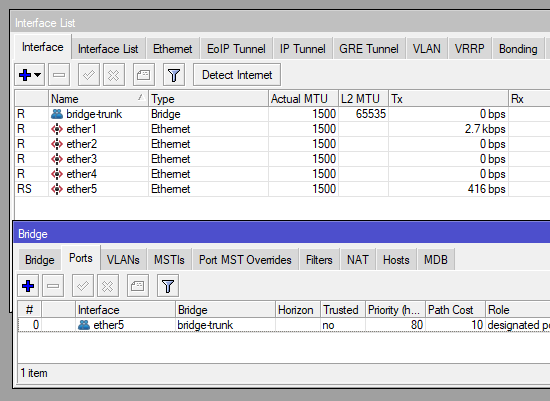
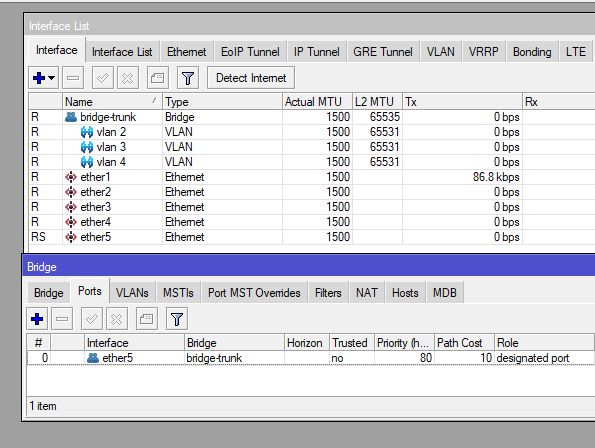
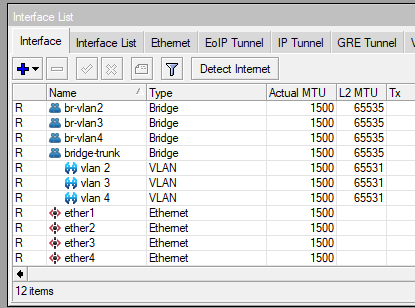
I will start this publication assuming you have a basic knowledge of the Mikrotik CLI and know your way around the interface.
This will also assume your firewall is empty, even though it may not be the case, you should be able to pick this one apart and chose what you like and skip what you don’t.
Some guides group the firewall rules by forward and input chains, but I like to group them by purpose, it seems better to me whenever you troubleshoot something.
Just know the Mikrotik firewall process rules in sequential order, this part is important.
So, to begin with the rules:
/ip firewall filter
add action=accept chain=input comment="Accept established & related inputs" \
connection-state=established,related
add action=accept chain=forward connection-state=established,relatedThe previous rules allows to avoid rechecking all packets passing through the router, this will save us CPU.
add action=drop chain=input comment="Drop invalid inputs & forwards" \
connection-state=invalid
add action=drop chain=forward connection-state=invalidThe previous rules will reject any invalid or malformed packets.
add action=reject chain=input comment="Reject blacklisted" in-interface=\
ether1-wan reject-with=icmp-network-unreachable src-address-list=\
BlacklistI like using blacklists to prevent malicious agents and IPs from reaching my router, this will make sense later.
add action=drop chain=forward comment="Drop all from WAN not DSTNATed" \
connection-nat-state=!dstnat connection-state=new in-interface=ether1-wanThis rule will drop inbound forwards that are not ‘NATted’, the rule effectively blocks inbound traffic that hasn’t been explicitly mapped to a destination on your internal network through DNAT.
add action=accept chain=input comment="Accept inputs from the whitelist" \
in-interface=ether1-wan src-address-list=WhitelistYou could skip this one, the purpose of this rule is to only allow the IPs you know to reach the router. Use this one carefully and please know there are better ways to access your router remotely, like through a VPN with wireguard.
add action=add-src-to-address-list address-list="Unknown Admin" \
address-list-timeout=1w chain=input comment="Log unknown admins" \
dst-port=8291 in-interface=ether1-wan log=yes log-prefix="Unknown Admin" \
protocol=tcp src-address=0.0.0.0/0
add action=accept chain=input comment="Accept unknown admins" dst-port=8291 \
in-interface=ether1-wan protocol=tcp src-address=0.0.0.0/0If you decide to keep the port 8291 open on the router, and I’m not saying you should, you may want to keep tabs on who is trying to access your router, this is the purpose of the rules above.
add action=accept chain=input comment="Accept inputs from home" in-interface=\
bridge.home src-address=192.168.88.0/24
add action=accept chain=forward comment=\
"Accept internet access for home devices" in-interface=home-bridge \
out-interface=ether1-wan src-address=192.168.88.0/24These rules allow your local LAN, configured on the bride called ‘bridge.home’ to reach your home router and to access the internet.
add action=add-src-to-address-list address-list=Blacklist \
address-list-timeout=1w chain=input comment=\
"Add forbidden attempts to the blacklist" dst-port=\
21-23,25,53,80,110,135,139,443,445,587,1025,1352 in-interface=ether1-wan \
protocol=tcp src-address=0.0.0.0/0 src-address-list=!Whitelist
add action=add-src-to-address-list address-list=Blacklist \
address-list-timeout=1w chain=input dst-port=\
1433,1433,1521,3306,3389,5060,5900,6001,8000-8080, in-interface=\
ether1-wan protocol=tcp src-address=0.0.0.0/0 src-address-list=!Whitelist
add action=add-src-to-address-list address-list=Blacklist \
address-list-timeout=1w chain=input dst-port=\
53,69,161,135-139,445,593,1433-1434,1900 in-interface=ether1-wan \
protocol=udp src-address=0.0.0.0/0 src-address-list=!WhitelistThis is the section of the blacklist, it will block any outside IP trying to connect to your router using any of the ports above.
If you are not exposing any services on your network to the outside world and there are IPs trying to access your network via any of the ports mentioned above, you’ll see them populate a blacklist in your router.
In my opinion, any public IP trying to reach your router on any of the ports above are looking for trouble.
add action=reject chain=input comment="Drop all from WAN" in-interface=\
ether1-wan reject-with=icmp-network-unreachable
add action=reject chain=forward comment="Drop everything else" reject-with=\
icmp-network-unreachableThe last two rules of the router are meant to drop any connection you may have not configured. It’s important not to skip these for security purposes.
Please note I’m not showing how to configure a NAT here, which you may need.